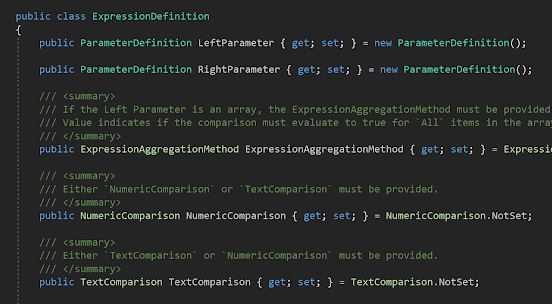
Auth0: Restrict SPA Application Access to API Audience/Permissions/Scopes

In Auth0 you can restrict the APIs/Permissions a Machine-to-Machine type Application has access to using the "APIs" section in the Application Configuration: However, SPA type Applications do not have an equivalent configuration option: There is no way to restrict the APIs a SPA type Application has access to directly . Instead, you must restrict the APIs/Permissions/Scopes a User has access to . (Most likely you'll want to do this using Roles.) You must also ensure the " Enable RBAC " setting is turned on for all of your APIs (this setting is off by default). If the "Enable RBAC" setting is NOT turned on, a SPA Application will be able to request a token for any API/Permission/Scope combination and Auth0 will return a valid token! And even with this setting turned on, a SPA Application will be able to request and receive a token for an API the user does NOT have access to! The Audience value in the access token will be valid for the API, however the