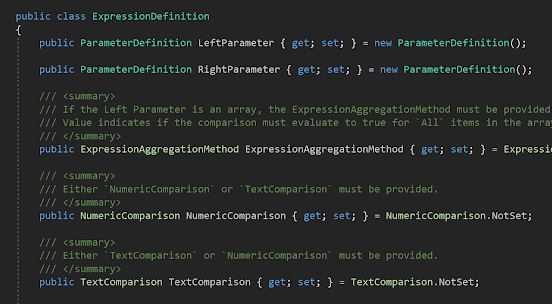
Find Azure Application Insights Resource by InstrumentationKey
I had a need to query some Application Insights logs, but all I had was the InstrumentationKey. I didn't want to open each of the Application Insights instances and check the key (there were a lot), but as long as you have the Azure "Az" Powershell Module installed, you can run this script to print out all App Insights instances and their associated Instrumentation Key: https://gist.github.com/aaronhoffman/cf5bd0c59216b3e6a57c0c6ea134cafb # for each subscription in context foreach ( $subId in ( Get-AzSubscription ).Id | Get-Unique ) { write-host " Subscription $subId " # set context to the given subId Set-AzContext - SubscriptionId $subId # List the name and InstrumentationKey of all Application Insights resources in this sub Get-AzResource - ResourceType Microsoft.Insights / components - ExpandProperties | select - ExpandProperty Properties | select Name , InstrumentationKey | ft } Hope this helps! Aaron